However, in 2015, when the Chinese government implemented strict regulations on VPN connections, Chinese-language discussions began appearing...
In the end, he was sentenced to life in prison for running one of the largest and...
These markets host hundreds, or in some cases thousands, of people who sell drugs, commonly referred to...
The name DisrupTor refers to the Tor Browser, the largest encrypted proxy network on the internet. Both European and...
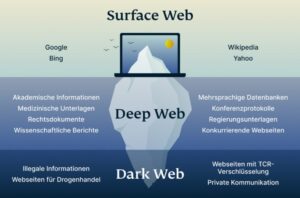
If you’re using a browser like Tor and visiting .onion websites that aren’t accessible through regular search...
Further market diversification occurred in 2015, as did further developments around escrow and decentralization. These background papers...
Further confounding efforts, these multiple markets are often scattered across different regions and jurisdictions, requiring significant international...
It demonstrates how international cooperation – particularly between Thailand, Interpol, and European law enforcement agencies – can...
Resecurity estimates this figure to be significantly higher in 2023, the annual sales of illegal drugs in the...
McDonald recruited and hired accomplices to help package and ship the narcotics they sold on the darknet....