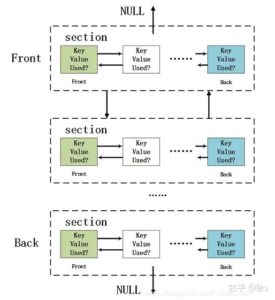
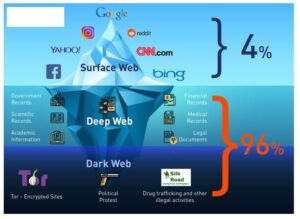
Even if you still have a regular in-person dealer that you trust, they may not know what...
These platforms leverage advanced encryption technologies, decentralized systems, and user-friendly interfaces to ensure seamless transactions. The integration...
While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make...
One of the few successful illustrations of coordinated actions was the seize of European DNM “ItalianMafiaBrussels” with...
There are about 7000 volunteer computers worldwide that serve as relays (Clemmitt 2016). Her work has appeared...
These markets also prioritize user feedback and reviews, allowing buyers to make informed decisions based on the...
It has a search option to let you find local and international products and services on the...
Between 2021 and 2024, Nemesis Market processed more than 400,000 orders. Of these, more than 55,000 orders...
“Over the years some markets … developed a robust catalog of illicit services like money laundering, fiat...
Additionally, the diversity of products available on darknet markets is unparalleled. From pharmaceuticals to digital goods, these...