Set Tor Browser’s security level to “Safest” for critical dark web activity. This disables potentially dangerous features...
Your data is encrypted in the Tor browser before reaching the ZeroBin servers. This is the best...
These patterns of misuse highlight a broader societal issue, where performance and productivity are prioritized over health...
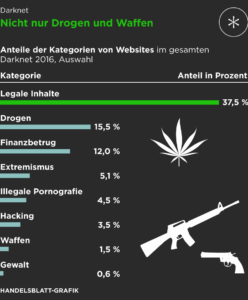
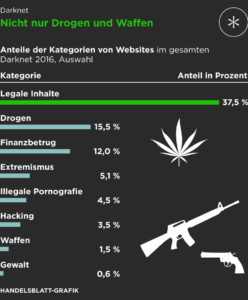
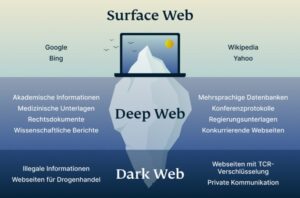
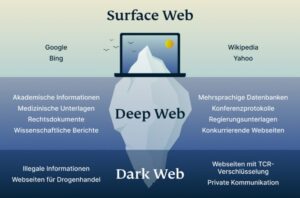
It focused on the darknet, which is a network that is not accessible by search engines like...
Yes, many darknet markets offer illegal goods and services, making them illegal in most jurisdictions. Engaging in...
In a way, it feels more like a private club than an open market, and that’s exactly...
Each server adds a layer of encryption, and this layered system is what lends The Onion Router...
Mars Market is a futuristic darknet platform designed for those seeking innovation, speed, and secure trade in...
This is a free service that lets you upload images to share them with other people. This...
It acts as your digital shield, protecting your personal information and ensuring your online activities remain private....