In fact, some parts of it actually provide a safe space for privacy and freedom, especially where...
darknet
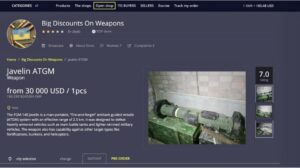
People visit this market to buy stolen credit cards, personal data, remote desktop account credentials, and logs...
But don’t expect the dark web’s downtime to last, says Roman Sannikov, an analyst at security firm...
To the best of our knowledge, a comprehensive overview of the opioid supply chain in the anonymous...
Buying directly from an online dealer—as opposed to through one of the marketplaces—is generally inadvisable. There’s no...
We then identified 311 opioid keywords and jargons to recognize 28,106 listings and 13,508 forum traces related...
‘People will say how reliable they were in getting the drugs to them, how long it took...
Overdose deaths involving heroin began increasing in 2000 with a dramatic change in pace, and as of...
To collect the listing information of 5 anonymous online marketplaces (ie, Apollon, Avaris, Darkbay, Empire, and The...
There are many different ways to access the dark web, but navigating it can be tricky and...