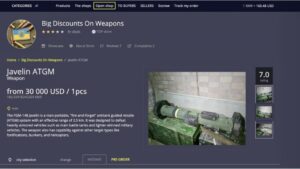
Dark-web marketplaces attract sophisticated cybercriminals adept at launching phishing scams, malware attacks, or ransomware threats. Buyers and sellers frequently face risks from malicious actors posing as legitimate vendors or customers, potentially leading to financial loss or exposure of sensitive personal information. Significant technological innovations and trends have reshaped dark-web marketplaces over recent years. In 2025, many platforms have adopted decentralized architectures, reducing single points of failure that previously made them vulnerable to law enforcement takedowns. You can use dark web monitoring tools, such as NordVPN’s Dark Web Monitor, to check if your data has been leaked.
Learn how dark web markets operate and why they pose a growing threat to your organization. No, many .onion sites serve legal and ethical purposes such as secure communications, anonymous sharing, and journalism support. Yes, Onion.live and Haystak provide real-time updates and search functionalities for .onion sites. DeepPaste is a .onion-based paste site where users anonymously share encrypted text, often containing code, leaks, or confidential messages. Haystak is an advanced search engine for the dark web that offers a vast database of indexed .onion pages, helpful for professional intelligence collection.
The 17 Best Dark Web Marketplaces In 2025
Another way to gauge people’s interest in the Dark Web is to examine the percentage of those who look up the term “Dark Web” on Google. Between January 2019 and September 2023, the majority of those queries came from underdeveloped countries with well-documented instances of internet censorship. Pakistan topped the list with 100 index points (maximum), followed by Kenya (89 points) and Myanmar (87 points). The top 10 also included Bangladesh (78), Ethiopia (75), Nepal (75), Cameroon (67), Tanzania (66), Nigeria (65), and Sri Lanka (63 index points). The aforementioned Tor browser has established itself as the go-to browser for accessing the Dark Web.
Are All onion Sites Illegal?
It includes all the essential productivity software, including MS Word and an email client. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web.
Is It Illegal To Visit A Dark Web Site?
The second category consists of data stores, which specialize in stolen information. In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years. If you want more peace of mind, NordVPN has a dark web monitoring tool you can consider using. This handy feature monitors the dark web for signs that your login details or other personal info have been leaked. Then, you can set up 2FA (two-factor authentication) for that extra touch of security in case someone somehow figures out your password. If you ever have to connect to public Wi-Fi, make sure to use a VPN to keep your browsing safe and private.
The Russian-linked Hydra Marketplace Had A $1 Billion Turnover In 2020
The Darknet is a subset of the Internet operating over encrypted, anonymous overlay networks that require special software like Tor, Freenet, or I2P. Many dark websites are set up by scammers, who constantly move around to avoid the wrath of their victims. Even commerce sites that may have existed for a year or more can suddenly disappear if the owners decide to cash in and flee with the escrow money they’re holding on behalf of customers. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape. The experience is reminiscent of searching the web in the late 1990s.
The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing. For this reason, you cannot browse through these sites using your default search engine. Just like Google, the dark web has some search engines present on it.
- Dark web forums are online platforms that can only be accessed using anonymous networks, mainly Tor….
- Similarly, there is no unique choice for the classification parameters or ground truth for fitting them.
- On the other hand, it’s notorious for enabling illegal activity, including drug sales, weapons trafficking, counterfeit ID trading, hacking services, and the exchange of stolen personal data.
- Therefore, if you do decide to explore it, exercise extreme caution.
- They’ve got 2FA and encryption that’s tighter than a drum, which I’ve tested against crash-prone sites and found solid.
Tor Averaged More Than 461 Million Daily Users In Q3 Of 2023

Businesses should be aware of the potential for data leaks and invest in data loss prevention measures. Credit card fraud, aka carding, is also a popular product category on Ares with well over 500 listings. Again, prices range dramatically as well as the types of products offered. Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details.
Deep Dive Into Darknet Markets Of 2025
Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with the use of this material. Some countries have just one or a few vendors with a loyal customer base and a wider selection of goods. For example, in India, one of the most frequent listings is for generic medication, which mostly comes from the first vendor shown below. While the US market is best characterized by its diverse product offerings, other countries offer regional specialties.
Unfortunately, it requires you to have an invitation code to create an account. This means you have to know someone who is already using the platform. Even without the code, you can visit the security section to get tips on improving your daily life privacy. Using the ProtonMail .onion site offers security and privacy advantages. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection.
Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. As mentioned earlier, launching a cyberattack doesn’t require any hacking skills. Even people with zero technical knowledge can buy phishing kits, ransomware, or stolen logins.
Track and analyze darknet activities using our advanced cyber threat intelligence platform to stay ahead of emerging threats. Archetyp Market was dismantled in June 2025 during Operation Deep Sentinel in a coordinated raid across six countries. At the time, it had over 600,000 users, 17,000 listings, and approximately €250 million in transactions. Authorities seized €7.8 million and arrested operators in Germany, Spain, Sweden, Romania, the Netherlands, and the US Europol leads takedown of Archetyp. BriansClub remains a long-standing credit card data shop since at least 2014.
How To Gain Safe Access To The Dark Web Marketplaces
This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session. A top-of-the-line VPN network that ensures maximum security while accessing dark sites online.

Cryptocurrencies, while offering enhanced privacy, also present significant risks. Users face vulnerabilities like market volatility, scams involving fake escrow services, compromised wallets, or theft through phishing schemes targeting crypto transactions. Furthermore, inexperienced users unfamiliar with secure cryptocurrency practices are particularly susceptible to these threats, risking the loss of their entire funds. Ideal marketplaces support anonymous browsing through networks like Tor and I2P, utilize privacy-focused cryptocurrencies such as Monero, and implement measures to prevent tracking and transaction tracing.
Since the dark web can be accessed through the Tor browser, use a VPN with the Tor browser to ensure increased protection. A VPN hides the fact that you’re using Tor, which is blocked in some countries and always raises doubts because of its criminal reputation. When visiting the dark web, use a secure browser like Tor, do not reveal any of your personal information, and don’t open suspicious files or links to stay safe. With over 20 years of experience in cybersecurity and marketing, Ben has held leadership roles at companies like Check Point, Cognyte, Cylus, and Ionix. It is not uncommon for vendors to use snark or humor in their advertisements, below we provide some real FAQs that are provided by the vendors.