
Free and paid tutorials on the dark web teach fledgling criminals how to use stolen credit cards. Monitoring the activity on these platforms is crucial for fraud detection, brand protection, and financial intelligence. Because of the level of anonymity, these sites allow cybercriminals, it is critical to use powerful dark web monitoring tools, such as Webz.io’ Lunar, to track emerging financial and reputational threats.
Data That Was Found And Suggested Next Steps
This online place, inaccessible by traditional search engines, is where stolen personal information can be sold anonymously. Resecurity identified multiple Chinese cybercriminal groups offering NFC-enabled POS terminals to facilitate fraudulent transactions and money laundering operations. The bad actors register these terminals with money mules, creating merchant accounts in various processing systems and financial institutions globally. Such fraudulent merchants have been identified in China, Malaysia, Nigeria, and South Africa. One of them, “HCE Bridge”, simulates and implements all six EMV Contactless Kernels, including PayPass, PayWave, Expresspay, J/Speedy, D-PAS, and QuickPass.
The use of such platforms is crucial for maintaining the integrity and security of customer data, and it provides an additional layer of defense against cybercriminal activities. The black market for stolen credit cards is a massive illegal business, with cybercriminals getting their hands on card data in a number of ways. Point-of-sale card skimmers, targeted Magecart attacks on websites and info-stealing trojans are among their top tools for stealing credit-card data. These illegal activities are made possible by the layer of anonymity provided by Tor and other similar networks.
How To Access The Dark Web Safely
Kim Komando hosts a weekly call-in show where she provides advice about technology gadgets, websites, smartphone apps and internet security. Credit card details with balances up to $5,000 go for $110, and online banking logins with $2,000 or more go for $60. Actual or formally correct ID card numbers are among the most expensive goods on the dark web. Interestingly, a major part of the carding ecosystem revolves around education.
The actors behind the tool provide technical support and guidance on how to use it. The dark web isn’t a single destination but a collection of anonymized networks where privacy is paramount. It was originally designed to protect free speech and privacy but has also become infamous as a marketplace for everything from counterfeit documents and illegal drugs to, you guessed it, stolen financial data. For many, it sounds like the plot of a spy thriller, but behind the drama lies a real risk for unsuspecting cardholders. The cybersecurity firm says the infostealer malware known as Redline was the most prevalent of the data-thieving malware, accounting for 34% of the total infections in 2024. Risepro, which primarily focuses on stealing banking card details and passwords, is another fast-spreading infostealer.
Among these are platforms dedicated to carding—a cyber crime niche centered on the large-scale use and abuse of stolen credit card information. The dark web is a hidden part of the internet that requires specific software to access. Within this clandestine realm, various illicit activities occur, including the trading of dark web credit cards. These cards are often stolen or compromised and circulate in underground markets. Threat actors have leaked 1 million stolen credit cards for free online as a way to promote a fairly new and increasingly popular cybercriminal site dedicated to…selling payment-card credentials. Be cautious when making online transactions, especially when it comes to sharing credit card information on the dark web.
Compromised Online Account

There’s a wealth of information shared among carders—from how to bypass anti-fraud systems to practical guides on using stolen credit cards—all of which helps keep the ecosystem active and evolving. Earlier this year, a New York man pled guilty to managing a credit card theft scheme responsible for stealing $1,500,000 from 4,000 account holders between 2015 and 2018. According to the United States Attorney’s Office, the ring of thieves obtained the credit card information on the dark web, and used that information to create their own cards.
Million Stolen Credit Cards Given Away Free On Dark Web Forum
Join us as we break down and discover the methodologies of card fraud using our dark web monitoring tool, Lunar. Judging from the activity on the shop, BidenCash appears to be thriving in 2023, providing an active data and money exchange platform in a market that has experienced a decline in recent years. This time, the leaked data contains card numbers, expiration dates, and three-digit security codes (CVVs). The expiration for most cards reviewed by BleepingComputer ranges from 2025 to 2029, but we also spotted a few expired entries from 2023. Contrary to popular belief, most carding platforms no longer hide in the dark web (i.e. the Tor network). The sites I’ve evaluated this year all had clear web addresses—with ‘.onion’ versions available for some of them.
WeTheNorth Market
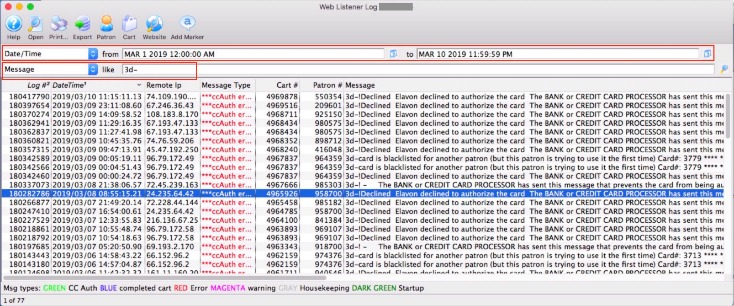
The threat actor mentions that the data is accompanied by a vulnerability report, with a combined price of $5,000. Organizations with greater cyber situational awareness will be able to detect and respond to these instances more quickly. The analysts claim these cards mainly come from web skimmers, which are malicious scripts injected into checkout pages of hacked e-commerce sites that steal submitted credit card and customer information. The “special event” offer was first spotted Friday by Italian security researchers at D3Lab, who monitors carding sites on the dark web. The first step you should take is to contact your bank or credit card issuer immediately.
- Your credit card data—and by extension, your financial future—is worth protecting.
- These details are primarily sought for physical use, enabling activities such as cash withdrawals from ATMs.
- This adaptability underscores the ongoing challenge faced by financial institutions in combating the ever-evolving threat of dark web credit card marketplaces.
- Simultaneously, customers face the risks of identity theft, damaged credit scores, and the emotional toll of financial fraud.
- By staying informed about these hidden risks and maintaining cautious online practices, individuals can better protect themselves from becoming victims of this shadowy aspect of the internet.
- If you notice anything unusual, contact your credit card company immediately to report the issue.
Privacy Affairs – a data privacy and cybersecurity research group – has analyzed the supply and pricing of these goods on the Dark Web and we’ve gathered some highlights. The dark web is the notorious ‘hidden’ side of the internet – hosting websites that cannot be found on Google and can only be accessed via special browsers. Cardholder verification is required for contactless card transactions above the CVM limit (e.g., by online PIN using the merchant PIN pad or signature). The merchant is liable for contactless transactions above the CVM limit that have no cardholder verification.

Inside The Surprisingly Sophisticated Marketing Of Carding
It is crucial for individuals to understand the link between credit cards and the Dark Web and take necessary precautions to protect their financial information. Understanding the Dark Web is crucial for detecting potential threats and taking necessary precautions to protect your credit card information. Now that we understand why individuals are enticed to buy credit cards on the Dark Web, let us explore the risks and challenges involved in these transactions and how to navigate this treacherous landscape.
- Learn the basics of credit card cards, including features, fees, and rewards to make informed decisions about your credit card usage.
- Others had been notified by a payment card processor that a theft had occurred.
- She combines her background in digital marketing from DePaul University with a passion for cybersecurity to create content that helps people and businesses stay secure.
- The cards belong to the Visa® or Mastercard® network and are accepted by vendors that accept U.S. credit cards.
These tools include for example different types of checkers, which assist threat actors in verifying whether the stolen card information they possess is valid and can be used to make unauthorized purchases. An estimated 1 million U.S. and global credit cards were released by a Russian criminal organization on the so-called dark web, according to analysts at cybersecurity firm Q6. The group, which calls itself “All World Cards,” offers stolen credit card information to other criminals. It has built a reputation for being a reliable source of stolen credit card data and PII. Renowned for its extensive inventory of financial data and sophisticated operating methods, Brian’s Club is a key player in the underground economy of financial cybercrime.
This adaptability underscores the ongoing challenge faced by financial institutions in combating the ever-evolving threat of dark web credit card marketplaces. Much like the situation after Silk Road was taken down, out of the ashes of Joker’s Stash, we have seen dozens of new carding data providers crop up, some specializing in particular regions or types of card data. Over the past decade, Joker’s Stash emerged as one of the most infamous dark web marketplaces, gaining notoriety for illicit transactions and offering a plethora of stolen financial data. The platform, distinguished by the sophistication of its administrators, left an indelible mark on the cybercrime landscape, and became the central marketplace for stolen card data, outclassing all competitors. It’s important to detect fraud when a threat actor is trying to use stolen payment information to make a purchase from your business.
Sellers—even using quirky pseudonyms—provide information about the card’s “reliability,” such as spending limits, recent activity, and sometimes even the cardholder’s name and billing address. Buyers, ranging from petty criminals to organized crime rings, use this information to commit fraud, purchase high-ticket items, or even launder money. Information from hijacked accounts connected with information from stolen social media accounts can also provide a lot of information that could help a fraudster imitate us during a scam attempt.



