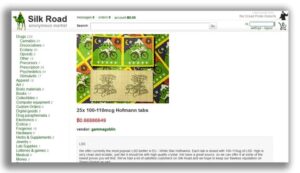
When it opened, Silk Road apparently prohibited the sale of anything with the intent to “harm or...
Uncategorized
No, it is not illegal to visit onion sites, but caution is advised as the dark web...
You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here. The Dark Web is...
Abacus Market appeared on the scene in 2021 and quickly became one of the heavyweights among English-speaking...
It works by sending internet traffic through volunteer-operated nodes all over the world. This network of over...
Although the site is still continually expanding and improving, it has become a significant resource on the...
If you’re curious about how to explore .onion sites safely and effectively, this guide will walk you...
It’s an interesting resource that translates Tor internet traffic levels into easy-to-digest stats. Riseup is available on...
Although Hidden Answers offers an outlet for anonymous dialogs, users should stay cautious while browsing. Posts on...
It means they search for .onion websites through automated means but also allow users to suggest new...