If you want to buy something, deposit cryptocurrency in your wallet, and you will be charged directly....
Uncategorized
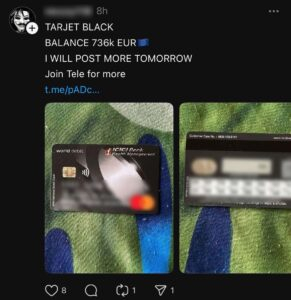
These markets mimic traditional e-commerce websites, but instead of second-hand books or vintage jackets, they traffic in...
The publicizing of Snowden’s actions led to a global spike of interest in Tor and a resulting...
In July 2024, the hacker group SiegedSec claimed responsibility for breaching the Heritage Foundation, a conservative think...
Two officials from the US Justice Department’s Child Exploitation and Obscenity Section told The Washington Post that...
We recommend using NordVPN as it offers top-notch security features, including dark web threat protection. Another disadvantage...
The dark web is often used for both legitimate and illicit purposes. On the legitimate side, it...
The hidden web (also known as the deep web or deep net) is the largest part of...
Let the ACM network’s editors and journalists bring you news and views from all over. Matthews declined...
They will notify you once your identity is used or listed for sale, helping you take steps...