Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only. Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks. The dark web is dangerous due to the presence of scams, malware, and illegal material.
Myth 4: The Dark Web Is Inherently Dangerous To Visit
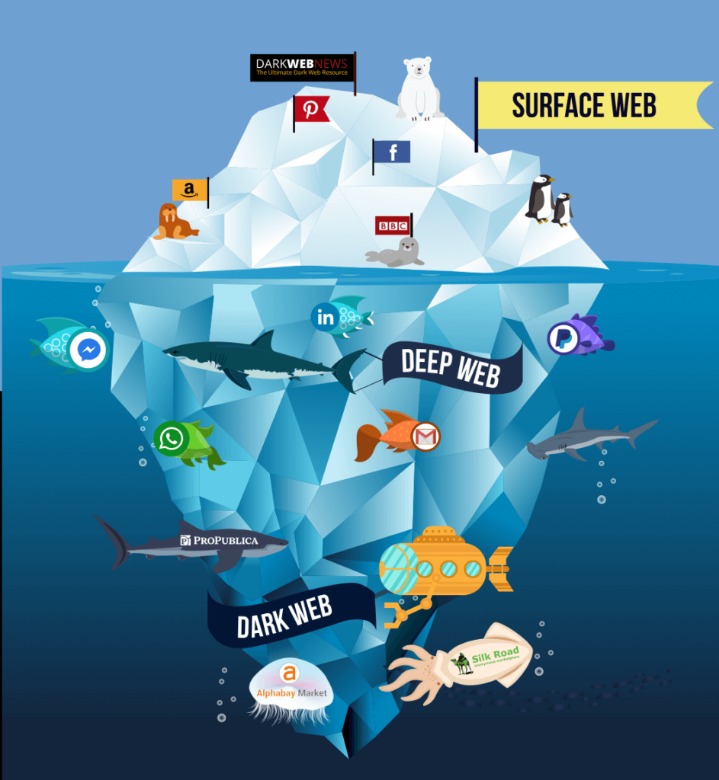
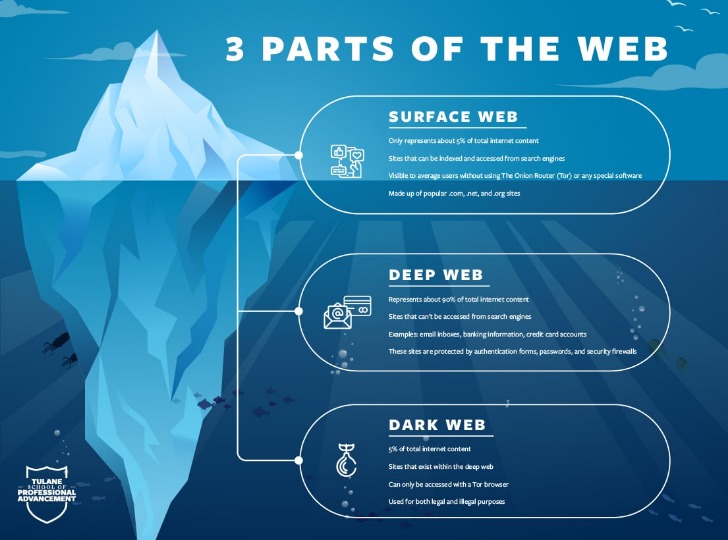
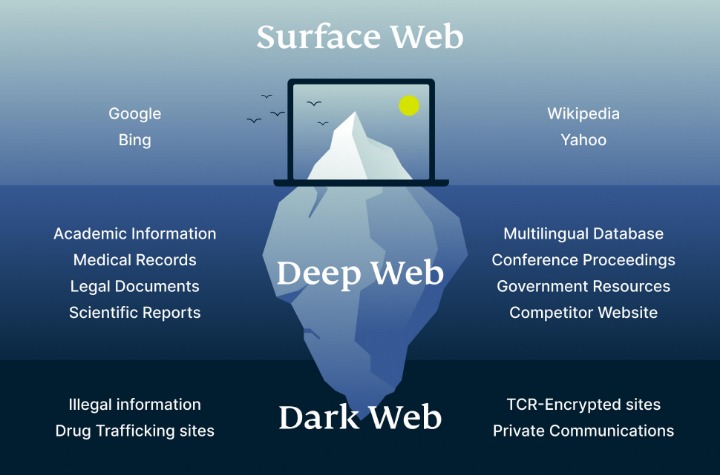
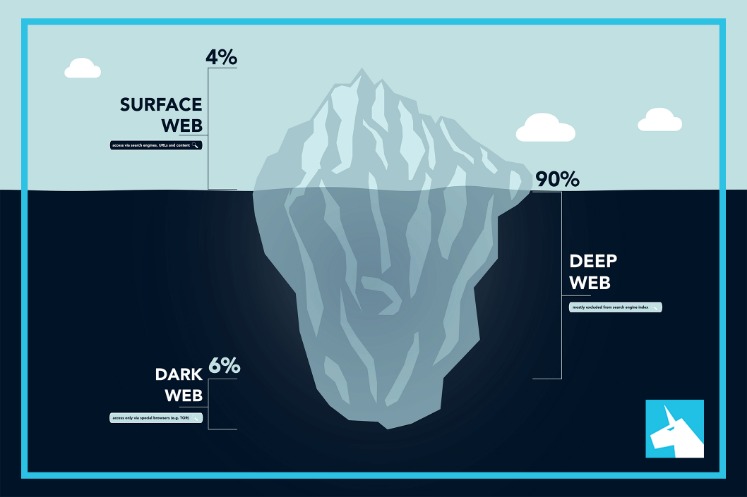
This makes it extremely difficult to trace where a request comes from or where it’s going. The dark web is a hidden part of the internet that stays out of reach for normal browsers and search engines. Unlike the websites you find on Google, the dark web uses special encryption and requires unique browsers like Tor to open its pages. Surfing it to commit illegal acts such as purchasing contraband or selling stolen data, however, is illegal and subject to law enforcement. The history of the Dark Web as a hidden network is tightly connected with the history of anonymous technologies and encryption.
Independent News Outlets And Investigative Journalism
Tor can be used together with a VPN to provide overlapping layers of privacy and anonymity. Unlike typical web browsers, Tor Browser uses onion routing, which encrypts and routes traffic through multiple servers around the world to hide your IP address and provide private browsing. In addition, all domains on the Tor network end with the top-level domain .onion (instead of .com).

More On How To Stay Safe On The Dark Web
We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch. It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address.
Install And Update Security Software
Tor, I2P, and Freenet are three common technologies that make up the dark web. For example, your Geekflare.com—your trusted business resource for growth exists on the surface web. To reach Geekflare.com, you can either type its URL in your standard web browser or search for Geekflare in your favorite search engine. Even completing a transaction is no guarantee that the goods will arrive. Many need to cross international borders, and customs officials are cracking down on suspicious packages.
Ways To Improve Cybersecurity Function While Spending Less
The dark web is a hub for ransomware tools and phishing kits that criminals sell or rent to launch attacks on people like you. Illegal software, fake documents, and hacking services are all part of this underground market. The dark web stays hidden through special tools like the Tor browser, which uses onion routing to protect user identities. In onion routing, your internet traffic is encrypted and bounced through multiple volunteer-run servers around the world.
The Different Types Of The Dark Web
While no approach guarantees complete safety, a careful and skeptical mindset serves as one of your most valuable tools on the hidden internet. This article aims to shed light on the more constructive side of the dark web, guiding readers toward reputable resources and reliable information. We’ll cover the foundational principles of anonymity on networks like Tor, discuss how to navigate this hidden realm safely, and emphasize the importance of verifying sources. Throughout, we’ll stress the ethical and legal considerations that come with exploring these lesser-known platforms. Knowing where online materials are – and who is searching for them – makes it possible for search engines like Google to sell advertisements.
Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin. The only difference is that it passes your traffic through random nodes before reaching the destination. This means your activities cannot be traced or your browser history exposed.
- We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch.
- For example, China uses the Great Firewall to block access to Western sites.
- You can use these dark web investigation tools to check if your company’s data is available on the dark web.
- The dark web is home to the internet’s hidden sites, services, and products — some innocent, others downright dangerous.
- After all, it enables users to connect and communicate with each other from around the world.
How Do I Get On The Dark Web?
- Hidden from everyday browsing beneath social networks and corporate websites are a number of sites, markets, and forums that make up what is known as the Dark Web.
- So, you risk being flagged or investigated for visiting certain sites, even without criminal intent.
- If you’re browsing a site with a “.onion” domain, you are on a hidden network.
- Some dark web commerce sites have dangerous chemicals and weapons for sale.
- And we pore over customer reviews to find out what matters to real people who already own and use the products and services we’re assessing.
Such architecture helps websites and services obscure their physical server locations. There are other ways for spies, hackers or other adversaries to target Tor. Lewis points to the “first contact problem”, when an attacker spots when someone moves from non-private tools to private ones, noting it’s been used to identify whistleblowers. However, the dark web has gained a negative reputation as a forum for those who want to use it for illicit activities.
This means that the JavaScript will be disabled by default on every website and some symbols and images will not be displayed. Advocacy groups are also reaping the advantages of the darknet because, here, the term of censorship is as popular as HTTPS. And finally, we have political outcasts, refugees, and people who want to get in touch with the outside world, being from a totalitarian country that suppresses all means of communication and information. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web.
Most links are accurate and still active, and each one includes a short description that’s usually spot-on. It’s a solid starting point for exploring, but it’s important to read descriptions carefully — some links lead to illegal or dangerous content. The dark web isn’t illegal in most places, but using the Tor browser can be. This special browser helps protect your privacy by masking your identity and hiding your online activity.
These onion addresses will remain online even if the original page disappears. It also keeps the graphical copy and text of the page for better accuracy. If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. The most common of these browsers is Tor, which launched in 2002 and serves millions of users.



