Hackers can gain access to Cash App accounts through phishing scams, credential stuffing, and brute force attacks....
Uncategorized
Our platform alerts security teams when an organization’s sensitive data is found. Breachsense monitors the dark web,...
Unfortunately, relying on the pen and counterfeit detector machines alone is not going to catch anyone other than...
If you’re prompted to connect, click the purple “Connect” button and wait for a few seconds. The...
But while you can’t undo a data breach, you can take control of what happens next. From...
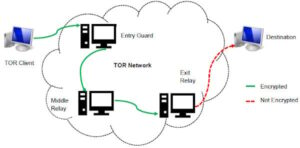
Though secure against everyday threats, Tor is vulnerable to targeted attacks from state-level actors. A common inquiry...
On the Tor network, the onion domain name reflects the fact that, like the layers of an...
Various cryptocurrencies such as Bitcoin and Monero can be used to make purchases. The Abacus Market links...
The bot recommends using wallets that have shown better performance with Lnp2pBot, such as Breez Wallet, Blixt...
According to Search Engine Land, in 2013, Google said that they knew about 30 trillion pages. In...