Each node decrypts just enough data to know the next destination but not the origin, making tracing the connection back to the user exceptionally difficult. No, while it hides your IP address and traffic, there are still vulnerabilities. Malicious exit nodes can monitor your traffic, and browser fingerprinting can track you.
Core Anonymous Networks And Protocols
You don’t want this suspicion because of the darknet’s reputation and notoriety. The entry node encrypts your traffic and it bounces across several nodes in the Tor networks until it reaches the exit node. This node decrypts your traffic and it reaches the destination i.e. the website you want to visit. The so-called surface web is readily accessible to all of us and thereby, less interesting. Well, relying on Tor to keep you anonymous online is a good recipe for disaster – we’ll see why soon.
How To Get On The Dark Web Safely & Anonymously In 2025?

Ask any tech question at facebook.com/DataDoctors or on X @TheDataDoc. You cannot stop breaches from happening, but good digital hygiene helps limit the damage and stay ahead of cybercriminals. We test each product thoroughly and give high marks to only the very best. We are independently owned and the opinions expressed here are our own.
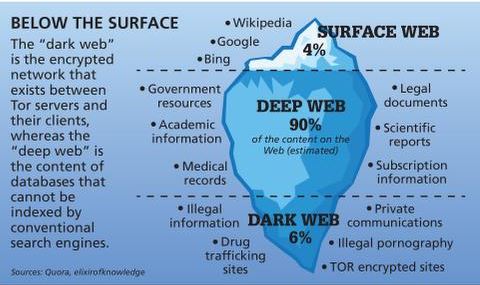
This would be the part of an iceberg beneath the water, much larger than the surface web. In fact, this hidden web is so large that it’s impossible to discover exactly how many pages or websites are active at any one time. Deep down, the tip of the iceberg is where over 90% of the internet content is. As much as the dark web is supposed to promote free speech alongside bypassing censorship, many shady activities occur there. Removing your sensitive personal information from the dark web once it has been exposed is virtually impossible.
As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity. While the Dark Web remains a core venue for privacy-seeking users and covert activities, a range of emerging platforms and shifting trends shape the broader ecosystem of underground communication. If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node.
Browse The Web More Safely
Venturing further into the deep web does bring a bit more danger to the light. For some users, portions of the deep web offer the opportunity to bypass local restrictions and access TV or movie services that may not be available in their local areas. Others go somewhat deeper to download pirated music or steal movies that aren’t yet in theaters. Locating surface web websites is possible because search engines can index the web via visible links (a process called “crawling” due to the search engine traveling the web like a spider). There are different levels of security in the browser that are worth considering.
Cybercrime Services
The dark web, being a hub for criminal activities like identity theft and malware distribution, exposes you to various security threats like malware or phishing. Using a VPN alongside Tor adds an extra layer of security by hiding your IP address from Tor entry nodes and encrypting your traffic. This prevents anyone—including your ISP—from knowing that you’re using the Tor network.
Can I Use A Free VPN To Safely Access The Dark Web?
- Here’s a step-by-step guide to setting up Tails on a USB thumb drive and using it to access Tor.
- To minimize the risk, research and verify sites before visiting them.
- Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination.
- ExpressVPN is my top choice because it supports Tor traffic on all of its servers and works automatically without needing any additional configurations.
- Although it’s not inherently illegal to access the Dark Web, remember that certain sites and activities may be.
Everything else, from academic journals to private databases and more illicit content, is out of reach. This deep web also includes the portion that we know as the dark web. There is a significant risk that the government can target you for visiting a dark website, as many Tor-based sites have been taken over by police authorities worldwide. Even if a person does not make any purchases on illegal marketplaces like the Silk Road, custom software used by law officials can analyze activity and identify user identities. A VPN encrypts your web traffic to ensure it’s hidden from the big brother who could be watching you online.

A Dark Web Search Engine
While the Tor Browser does an excellent job of protecting your privacy and anonymity, you really shouldn’t use it as your daily driver browser. Also, since the Tor Browser is based on the Mozilla Firefox platform, it’s susceptible to the same attacks that other browsers are. Go to the directory where you downloaded the Tor Browser installation file. Right-click on the downloaded file and select “Extract Here.” Once the Tor Browser setup files have been extracted, double-click on “Tor Browser Setup” to install the browser.

By following these tips, you will be better equipped to navigate the dark web effectively and make the most of your DuckDuckGo search experience. Explore this FAQ section to get answers to some common queries about this hidden part of the internet. Secure your online accounts with unique, strong passwords that are difficult to crack, such as a combination of uppercase and lowercase letters along with numbers and special symbols. In an era of rising digital surveillance and increasing cybercrime, the dark web represents both a warning and a tool. Use it to understand the boundaries of online freedom—and if you choose to explore it, do so with care, purpose and respect for the laws that govern your digital footprint.
Dangerous And Disturbing Services And Items
It’s important to note that Tor Browser may run slower than traditional browsers due to the encryption and multiple relays used to route your internet traffic. This is a trade-off for the increased privacy and anonymity it provides. However, engaging in illegal activities on the dark web, such as purchasing illicit goods, remains illegal, just as it would be on the surface web. Always connect through a VPN like Forest VPN to encrypt your connection and protect your identity.
The dark web is a murky part of the internet that isn’t accessible via a normal browser — and can be dangerous to visit if you don’t know what you’re doing. We’ll show you how to access and browse dark web sites, and how using a VPN to encrypt your connection can help you visit the dark web more securely. I2P is a private network built for secure, anonymous communication. Instead of the onion routing Tor uses, I2P relies on unidirectional tunnels and garlic routing, which bundles multiple messages together for better traffic obfuscation. It uses its own internal DNS to access “eepsites”, not .onion addresses. Now that you understand the essentials of anonymous networks and how to prepare yourself for secure browsing, it’s time to explore the practical steps involved in accessing the Dark Web.
- Examples include Ahmia, which filters out illegal content and offers a safer search experience, and Torch, known for its extensive index of dark web sites.
- The deep web is just the part of the internet you can’t find with a search engine.
- When people go on about the so-called dark web, they’re usually talking about onion sites, which aren’t searchable via Google or accessible via standard browsers.
- Although browsing the dark web is not illegal, it contains unsavory activities that can expose you to danger.
- On Tor, you can type in any URL you’d like to visit, including .onion links on the dark web.
Discovering The Dark Web: A Safe Exploration Guide
The dark web is a hidden part of the internet that isn’t indexed by traditional search engines and requires special software like Tor to access. It’s often used for anonymity, both for legitimate privacy reasons and for illegal activities like black market trading or data leaks. The dark web is a hidden part of the internet not indexed by regular search engines, accessed through specialized browsers like Tor.



