In July 2024, the hacker group SiegedSec claimed responsibility for breaching the Heritage Foundation, a conservative think tank. The group released internal communications and documents, alleging the breach was in protest against the organization’s political activities. Between June and August 2024, Japanese publisher Kadokawa and its video-sharing platform Niconico suffered a ransomware attack by the Russian-linked hacker group BlackSuit.
Pokemon Developer Game Freak Data Leak
Pretty much everything you would need to commit credit card fraud or launch phishing attacks against the cardholder. As B1ack’s Stash prepares to release its trove of stolen credit cards, law enforcement agencies and cybersecurity firms are working around the clock to trace the origins of these breaches and prevent further exploitation. Card data on the dark web is a valuable commodity, and it’s often sold on specialized marketplaces known as Card Shops.

The attackers secretly altered a digital wallet address, redirecting 401,000 Ethereum coins to their own wallet. The data, accessed through the university’s single sign-on system, included demographic, enrollment, and academic progression details. Hackers are now emailing school officials across the U.S. and Canada, demanding bitcoin payments. Exposed data includes Social Security numbers, medical records, and special education information. A vendor reported their Whole Foods product launch was stalled due to delivery issues and lack of communication.
Ascension Health Ransomware Attack
Find out precisely where attackers are targeting you and how to get there first. Join host Becky Bracken and Uptycs researchers Amit Malik and Ashwin Vamshi on Aug. 17 at 11AM EST for this LIVE discussion. Some fullz even include photos or scans of identification cards, such as a passport or driver’s license.
Your Credit Your Identity
You can also consider using a credit monitoring service to alert you to any changes in your credit report. Staying vigilant and proactive can minimize your risk of falling victim to credit card fraud. Regularly monitor your accounts, use secure connections and invest in tools like credit monitoring services for additional peace of mind. Leaking credit card credentials has become a very common phenomenon on chat applications, particularly Telegram.

Million Stolen Credit Cards Given Away Free On Dark Web Forum
- Fullz that come with a driver’s license number, bank account statement, or utility bill will be worth more than those without, for example.
- An employee exposed a GitHub token in a public repository, giving access to the company’s systems, including source code, cloud keys, and API credentials.
- While the vendor’s name remains undisclosed, early signs suggest the breach is part of a broader series of attacks on external CRM platforms.
- In March 2025, the New South Wales Department of Communities and Justice (DCJ) experienced a significant data breach involving unauthorized access to the state’s secure online court registry system.
- The vast majority (98% of the records) came from Indian banks, Group-IB said in its threat report.
- BidenCash is a stolen cards marketplace launched in June 2022, leaking a few thousand cards as a promotional move.
Verified by Visa is a service that prompts the cardholder for a one-time password whenever their card is used at participating stores. When possible, using a credit card instead of a debit card is a good move too. You may have never been to the dark web — but there’s a chance your credit card information has. This tactic mirrors similar marketing stunts by other illicit platforms, such as BidenCash, which leaked 2 million cards in 2024 to celebrate its anniversary.
Recommendations For How To Combat Stolen Financial Data
On these forums, actors will often share techniques, hacking tools, strategies, and resources for conducting fraudulent activities. Access helpful services and useful information to help you take control of your credit report, and better protect yourself from identity theft and fraud. In July 2024, Comcast reported a data breach involving over 230,000 customers.

How War Impacts Cyber Insurance
The campaign escalated tensions in a decades-long territorial dispute over land near the Preah Vihear Temple, a UNESCO site the UN’s International Court of Justice has repeatedly ruled belongs to Cambodia. In June 2025, the ShinyHunters group, tracked as UNC6040, compromised one of Google’s corporate Salesforce CRM instances. The breach affected prospective Ads customers, mainly small and medium businesses. Google confirmed there was no impact on Google Ads, Google Cloud, or other product data.
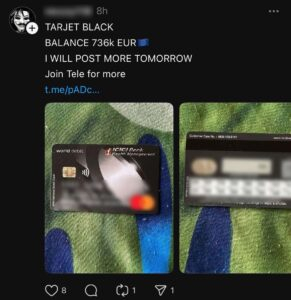
Why Cardholder Data On Threads Is A Growing Risk For Fraud & Security Teams
The breach originated from unauthorized access to a cloud database hosted by a third party provider, believed to be Snowflake, though Snowflake has denied involvement. In June 2024, the hacking group IntelBroker claimed responsibility for multiple cyberattacks, including breaches of Apple and AMD. Department of the Treasury disclosed a cybersecurity breach attributed to a state-sponsored actor from the People’s Republic of China.
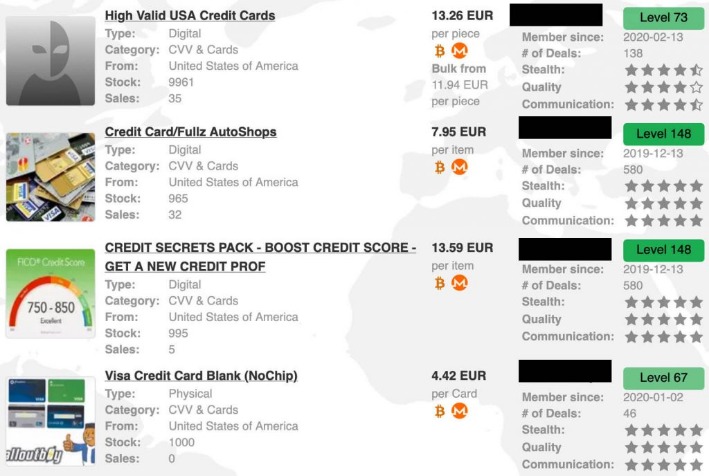
Fullz includes full personal details as well as financial details such as bank account details or social security numbers, which can be used for a full account takeover or identity theft. Carding shops are a type of dark web marketplace that hosts the trade of credit cards and other stolen financial information. These platforms serve as hubs for cybercriminals to buy and sell compromised payment card details.
Criminals Are Selling Millions Of Stolen Credit And Debit Card Numbers On The Dark Web
There are of course many ways to skin this proverbial feline, but it can be illuminating (possibly concerning) to see the actual steps involved. Let’s start right out with a step-by-step overview of the whole process, and then we’ll dive into some of the specific tools and methods that cybercriminals use in more detail. Post the dismantling of Joker’s Stash, cybercriminals displayed adaptability by establishing new marketplaces to fill the void, highlighting the resilience of criminal enterprises. This adaptability underscores the ongoing challenge faced by financial institutions in combating the ever-evolving threat of dark web credit card marketplaces.
He showed off his account on Deliveroo, a British online food delivery company, where he had 65 credit cards saved. Using a public Wi-Fi network for payments is a major security risk as hackers can easily intercept the transmitted data. Unsecured Wi-Fi networks are prone to man-in-the-middle attacks, where a hacker intercepts the exchange between two parties—often by compromising the router—and gains access to sensitive data. Discover the pros and cons of using credit cards or card for purchases, including benefits and risks, to make informed financial decisions. Card checkers are tools used by threat actors to verify the validity and authenticity of credit card information they purchase on the dark web. A second major leak of cards relating to Indian banks has been detected by Group-IB, with over 1.3 million credit and debit card records being uploaded to the Joker’s Stash marketplace.



