
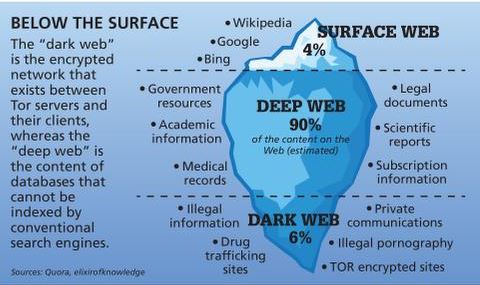
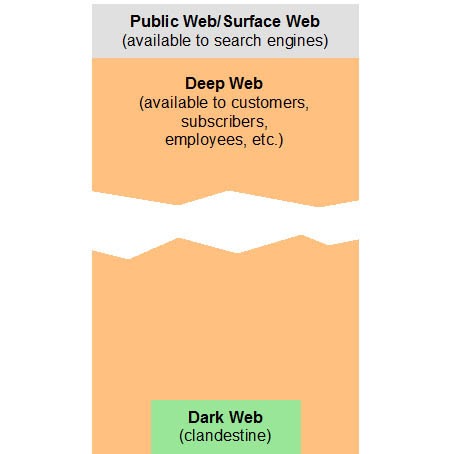
Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people. Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship.
How To Access The Dark Web Safely
Depending on your preference, you can find links in well-categorized groups. These categories include email providers, news sites, privacy, and commercial services. SecureDrop is a really awesome Tor service that can be used to share information without revealing your identity.
Bonus: A Few More Dark Web Websites
With each random server, your traffic bounces off, and a layer of encryption gets added. These layers upon layers give this network its iconic “onion” name—as the onion itself has layers upon layers. Like regular browsers with domain names, the Tor browser also has its own domain designation. These “onion” sites are only accessible on the dark web and bear the “.onion” domain at the end of the URL.

Legitimate Reasons Why People Use The Dark Web
Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe. You risk being targeted for attacks if you explore the dark web without protection. The threat can extend to your entire network of devices connected to the internet. In some countries, evading government restrictions to seek new political ideologies is punishable. For example, China uses the Great Firewall to block access to Western sites.
How Do I Browse Onion Sites Safely?
Additionally, we provide detailed descriptions and safety advice for each link, empowering users to make informed decisions. Unlike many alternatives that allow user submissions without thorough vetting, we prioritize quality over quantity to maintain a safer browsing experience. Our dedication to transparency and user security makes our directory a superior choice for navigating the dark web in 2025. Because the Hidden Wiki aggregates many links, it often contains outdated or malicious URLs disguised as legitimate ones.
SecureDrop — Secure File Sharing For NGOs, Journalists & News Organizations
Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions.
What Are Onion Sites And Dark Web Websites?
- The New York Times can also be anonymously accessed via the dark web.
- To access this marketplace, you must register, but before that, you must verify yourself as a human by passing a CAPTCHA test.
- It uses TrustedServer technology on the entire server network to wipe out your data after every session.
- Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement.
The marketplace has several rules that every user is bound to follow. If any user is found not complying with the law, strict and immediate action will be taken against them. It uses PGP encryption to protect sensitive data and messages, and accepts payments via Monera and Bitcoins to keep you anonymous on this marketplace.
However, many journalists, political activists, and agents also use the dark web when they need a secure way of communicating. No matter what you want to use the dark web for, it’s important to do it safely. If you’re looking for dark web urls or you know someone looking for deep web links, here is a working list of .onion links that will take you to the most popular Tor websites.
With its sleek UI and powerful search tools, Vortex makes it easy to navigate thousands of listings with confidence. Combining robust encryption, flexible payment options, and responsive support, Vortex is engineered for those who value both efficiency and anonymity. TorZon is a well-known name in the darknet landscape, recognized for its streamlined marketplace experience and long-standing presence in the community. Since its emergence, TorZon has focused on providing a secure and anonymous environment for users seeking privacy and stability. With a clean interface, reliable uptime, and active vendor support, it continues to stand out as a trusted hub for darknet commerce.
Haystak also offers a premium version that allows advanced search, access to historical content, and email alerts. Your real information could be exposed at these nodes, allowing third parties to intercept your dark web activity. That’s why we recommend connecting to VPN before accessing Tor—VPN encryption protects your data, and changing your IP adds an extra layer of privacy to protect you.
Our goal is to empower you with reliable information and resources, making your dark web experience as secure and informed as possible. Clicking a bad link on the dark web can expose you to phishing scams, malware infections, or honeypots set up by law enforcement. These malicious sites may attempt to steal your personal information or compromise your device’s security. If you suspect you’ve clicked a dangerous link, immediately disconnect from the internet, run a full malware scan, and change any passwords that may have been exposed. Be mindful that not all content on the dark web is legal or safe; avoid engaging with illicit activities or sites promoting harmful behavior.
However, DuckDuckGo doesn’t index dark web content — it only accesses surface and deep web sites through Tor. The dark web contains content that’s only accessible through networks like Tor. Tor browsers create encrypted entry points and pathways for the user, so dark web activity remains anonymous. The encryption technology routes users’ data through a large number of intermediate servers, which protects the users’ identity and guarantees anonymity.



