Its emphasis on user anonymity and document forgery makes it a core tool for identity fraud. Founded in 2014, BriansClub remains one of the oldest and most infamous dark web markets for stolen credit cards, fullz (complete identity kits), and dumps. This has curtailed user confidence and stunted the ecosystem’s growth, creating a climate of distrust that is reminiscent of the aftermath of Op. Onymous (the law enforcement takedown of the Silk Road 2.0 darknet marketplace together with a host of smaller DNMs in 2014) and Op. Bayonet/GraveSac (the coordinated takedown of the AlphaBay and Hansa Market darknet marketplaces by US and European law enforcement in 2017), which left the Western DNM ecosystem reeling. Last week, one of the dark web’s most prominent drug marketplaces – Archetyp – was shut down in an international, multi-agency law enforcement operation following years of investigations.
It’s known for its strong security features (like a trusted escrow system, PGP two-factor authentication) and anonymity. One of the things STYX is infamous for is having a rigorous verification process for users that makes it seem more exclusive. They even have a Telegram channel to provide their clients with live updates. Like most of the markets, STYX supports Bitcoin (BTC), Monero (XMR), and other crypto tokens to keep everyone’s identity hidden on this marketplace. While this market started in Canada in 2021, WeTheNorth now sells to both Canadian and international users. It’s a market for fake documents, hacking software, and financial fraud services.
Red Flag 3: Multi-product Rapid Movement Of Funds
During her free time, she can be found reading, baking, or getting zen on her yoga mat. However, it should be highlighted that these are recent developments. The very existence of fentanyl within the nation acts as a sobering reminder of the urgent need for not only enhanced drug enforcement measures moving ahead, but also greater public awareness.
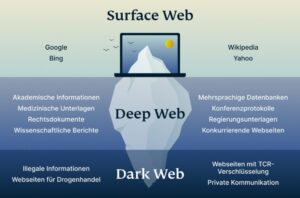
This is because law enforcement often actively monitors these sites. Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people. Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. It is easily accessible by the general public and requires no special configuration.
The flavour “magic mushroom” instead contains no organic properties like psilocybin, which experts agree is far safer than the drugs listed above. Psilocybin, or MDMA, has been experimented for post-traumatic stress disorder (PTSD) and depression treatment, although its efficacy is still being debated. He noted that children who have grown up in a tech-saturated environment – always having a device, always online, always on the internet – are, in many instances, more tech-savvy than their parents. Akhbar said that Malaysia had set up the National Cyber Security Agency in 2017 to serve as the national lead agency for cybersecurity matters. In an interview with The Vibes, he said the dark web can only be accessed by a special browser known as TOR, an abbreviation for “the onion routing”.
- “There has been a noticeable shift from traditional narcotics to synthetic alternatives, partly due to social influence and trends,” he added.
- “The volatility, accessibility and reliability of Tor and other dark web network-powered sites are a challenge for collection systems.
- Therefore, most cybersecurity experts recommend using Monero while shopping on darknet markets.
- At this point, we would like to highlight that the Tor browser is by no means the only browser that enables users to visit the dark web.
This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. A virtual private network (VPN) is a good way to mask Tor activities. It adds an extra encryption layer and passes your traffic through a secondary server of your choice, preventing anyone from seeing that you are accessing the web via Tor. Most likely, the native account on your device has full admin permissions by default. Many malware take advantage of this vulnerability to launch an attack.
Malaysia’s Progress In The Drug War
If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. This includes using an anonymous browser like Tor, a VPN to encrypt your connection, an antivirus for protection against malware (we recommend TotalAV), and generally being careful not to reveal personal information. If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself.

Listed items were mainly advertised as “safe” substitutes for medicinal products for the self-management of pain and other health conditions and offered in various forms (e.g., dry leaf powder, pills, capsules). Purchases were made using cryptocurrencies, with some vendors offering Pretty Good Privacy, and were shipped from Europe, Australia, the United States, and the United Kingdom. Goods sold by the same sellers also included illicit drugs and fraud-related products.

Category Deep-dive: Illicit Drug Sales Grew And Expanded Outside Of Darknet Marketplaces In 2024
Some sellers offer cracked versions of expensive software that you’d typically pay hundreds of dollars for. Others sell pirated eBooks, academic materials, and entire premium courses ripped straight from paid platforms. Want to get illegal drugs, fake passports, Trojan, or other cyber attack software? Plus, there’s a thorough vetting process for new buyers and sellers to keep the community more secure.
Police Shut Down Long-running Dark Web Drug Market
In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing. Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software. Immediately change your passwords, enable two-factor authentication, and notify your bank or credit card provider if the leaked information includes your financial data. You should also consider freezing your credit to prevent identity theft.
How To Access Cipher Market (cipher-marketto)
What current policing strategies neglect is that dark web markets are not isolated to the storefronts that are the popular target of crackdowns. These are communities stretched across dark and surface web forums which develop shared tutorials and help one another adapt to any new changes. These closures bind users together and foster a shared resilience and collective experience in navigating these environments. According to the director-general, Sutekno Ahmad Belon, findings by authorities indicate that the dark web and social media platforms have become the latest go-to sources for drug supply among addicts. We don’t want to leave you with the impression that everything on the dark web is nefarious or illegal. The Tor network began as an anonymous communications channel, and it still serves a valuable purpose in helping people communicate in environments that are hostile to free speech.

One Of The Most Popular Dark Web Markets
Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Some users also share links on encrypted apps like Telegram or Keybase that you can check. RiseUp is a top dark web website that offers secure email services and a chat option. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. The platform is protected from government interference and malicious attacks to protect the user. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for.
- However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities.
- Furthermore, many of the sites have defence mechanisms to detect and disable the automated scraping engines,” he says.
- Keep in mind that you’ve to use very specific keywords when searching.
- Transactions are encrypted, anonymized, and hardly visible to investigative authorities.
- Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content.
Is Using The Tor Network Illegal?
It scans darknet marketplaces and hacker forums to alert you instantly if anything shows up. This way, you can catch any leaks and stop them before they cause bigger problems. And, of course, think twice before sharing too much personal details online. Even the smallest details about you can be useful to cybercriminals. That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web.
Such content fuels a dangerous cycle of abuse, violence, and exploitation. The marketplace supports multiple payment methods, including Bitcoin (BTC), Litecoin (LTC), and Cryptocheck. They add new batches of stolen data every other week, and there’s even a bidding system where buyers can place offers on new data batches as soon as they become available. Now, that is not to say illegal behavior is completely beyond detection. The dark web combines encryption, anonymity, and hidden doorways to provide the perfect sanctuary for such illicit activity compared to the usual internet, which is more vulnerable and trackable. Given the explosive growth of these markets, organizations must prioritize proactive threat monitoring.
Why Is It Critical To Monitor Dark Web Marketplaces?
It allows you to search for images, maps, files, videos, social media posts, and more. Sci-Hub is a massive database that eliminates the barriers to getting scientific knowledge. It contains millions of scientific research documents from around the world. The site seeks to liberate information by making it free to individuals and institutions.